User-owned repository
Avatar shows a personal profile icon, URL includes username
This page describes authorization settings for GitHub Agentic Workflows, including:
You will need one of the following GitHub Actions secrets configured in your repository to authenticate the AI engine you choose:
COPILOT_GITHUB_TOKENANTHROPIC_API_KEYOPENAI_API_KEYDepending on what your workflow needs to do, you may need additional GitHub tokens added as repository secrets:
GH_AW_GITHUB_TOKENGH_AW_PROJECT_GITHUB_TOKENGH_AW_AGENT_TOKENGH_AW_GITHUB_MCP_SERVER_TOKENYou can add secrets manually in the GitHub UI or use the CLI for a streamlined experience.
gh aw secrets set COPILOT_GITHUB_TOKEN --value "YOUR_COPILOT_PAT"You can also check existing secrets with:
gh aw secrets bootstrap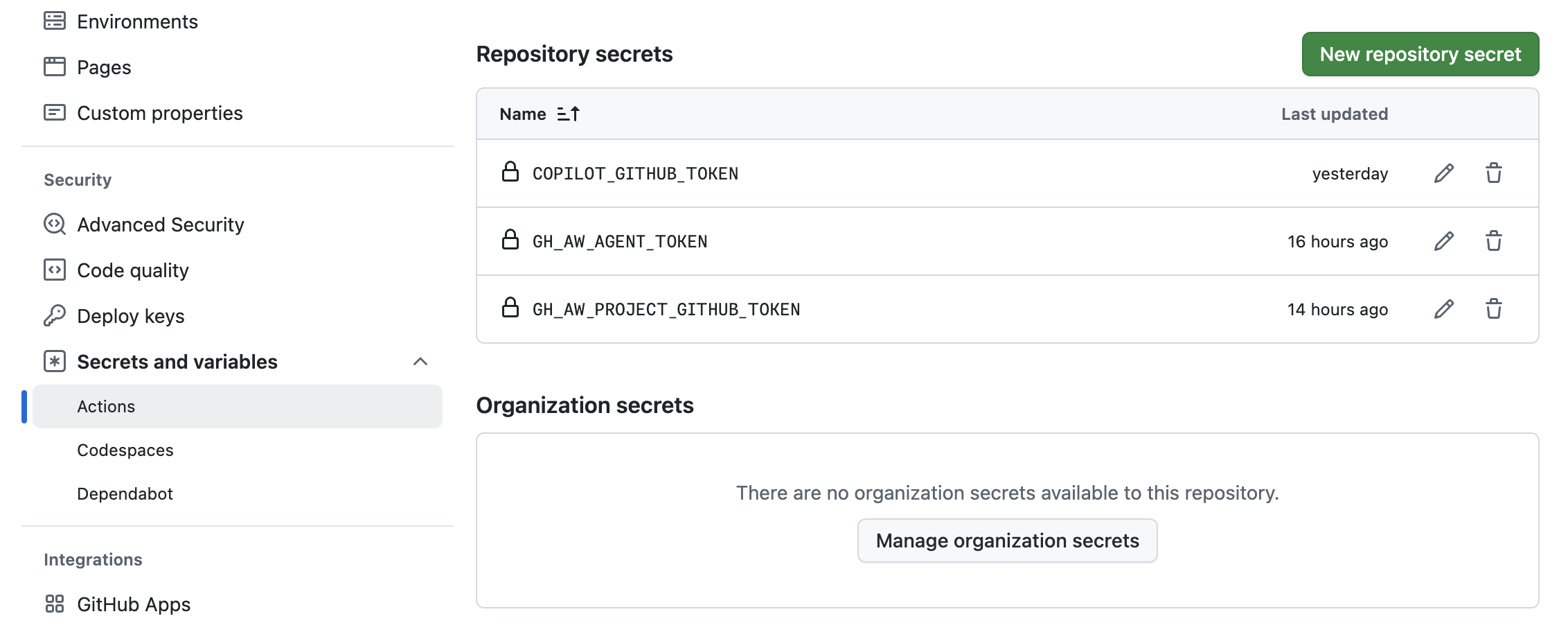
A reference for all GitHub Actions secrets and tokens used by GitHub Agentic Workflows, including when they are needed and how to set them up.
COPILOT_GITHUB_TOKENIf using the Copilot CLI, you need a GitHub Actions Secret set to a GitHub Personal Access Token (PAT) with the copilot-requests scope to authenticate Copilot CLI.
Setup:
Create a fine-grained PAT:
You must have “Public repositories” selected; otherwise, the Copilot Requests permission option will not appear.
Then add the PAT to your GitHub Actions repository secrets as COPILOT_GITHUB_TOKEN, either by CLI or GitHub UI (see video).
gh aw secrets set COPILOT_GITHUB_TOKEN --value "<your-github-pat>"ANTHROPIC_API_KEYIf using the Claude by Anthropic engine, you need to set a GitHub Actions secret ANTHROPIC_API_KEY to be an API key from Anthropic.
Setup:
Create an API key at https://platform.claude.com/docs/en/get-started
Add it to your repository secrets:
gh aw secrets set ANTHROPIC_API_KEY --value "YOUR_ANTHROPIC_API_KEY"See also (/gh-aw/reference/engines/#using-claude-by-anthropic-claude-code) for additional configuration needed when using Claude with GitHub MCP.
OPENAI_API_KEYIf using the Codex by OpenAI engine, you need to set a GitHub Actions secret OPENAI_API_KEY with an API key from OpenAI.
Setup:
Create an API key at https://platform.openai.com/api-keys
Add it to your repository secrets:
gh aw secrets set OPENAI_API_KEY --value "YOUR_OPENAI_API_KEY"See also (/gh-aw/reference/engines/#using-openai-codex) for additional configuration needed when using Codex with GitHub MCP.
GH_AW_GITHUB_TOKENA Personal Access Token (PAT) with appropriate scopes and permissions for enhanced security and cross-repository operations.
When Required:
lockdown: true is set in workflow frontmatter. The workflow will fail at runtime if the token is not configured.Note that using GH_AW_GITHUB_TOKEN replaces the default behaviour of GitHub Agentic Workflows (which arranges temporary GITHUB_TOKEN GitHub Actions tokens appropriate to the permissions: you have declared).
GH_AW_GITHUB_MCP_SERVER_TOKENIf you need different permissions for the GitHub MCP server than the default, you can configure GH_AW_GITHUB_MCP_SERVER_TOKEN with a Personal Access Token (PAT) or use a GitHub App for enhanced security.
Use this when you need different permission levels for MCP server operations versus other workflow operations.
When to use:
Setup:
Create a fine-grained PAT with:
Then configure in your workflow frontmatter:
permissions: contents: read issues: read
tools: github: mode: remote # or "local" for Docker-based toolsets: [repos, issues, pull_requests] github-token: ${{ secrets.GH_AW_GITHUB_MCP_SERVER_TOKEN }}Or add to repository secrets:
gh aw secrets set GH_AW_GITHUB_MCP_SERVER_TOKEN --value "YOUR_MCP_PAT"GH_AW_PROJECT_GITHUB_TOKENIf using GitHub Projects v2 operations, you need to configure this GitHub Actions secret with a Personal Access Token (PAT) that has the appropriate scopes and permissions for Projects access.
This is specialized token for GitHub Projects operations, required because the default GITHUB_TOKEN cannot access the Projects API.
When to use:
update-project, create-project-status-update safe output.Setup:
The required token type depends on whether you’re working with user-owned or organization-owned Projects:
For User-owned Projects:
You must use a classic PAT with the project scope. Fine-grained PATs do not work with user-owned Projects.
project (required for user Projects)repo (required if accessing private repositories)For Organization-owned Projects (v2):
You can use either a classic PAT or a fine-grained PAT:
Option A: Create a classic PAT with project and read:org scopes:
project (required)read:org (required for org Projects)repo (required if accessing private repositories)Option B (recommended): Create a fine-grained PAT with:
Option C: Use a GitHub App with Projects: Read+Write permission
After creating your token, add it to repository secrets:
gh aw secrets set GH_AW_PROJECT_GITHUB_TOKEN --value "YOUR_PROJECT_PAT"Token precedence and fallback:
per-output -> workflow-level -> GH_AW_PROJECT_GITHUB_TOKEN -> GITHUB_TOKEN.
Example configuration:
---# Option 1: Use GH_AW_PROJECT_GITHUB_TOKEN secret (recommended for org Projects)# Just create the secret - no workflow config needed---
# Option 2: Explicitly configure at safe-output levelsafe-outputs: update-project: github-token: ${{ secrets.CUSTOM_PROJECT_TOKEN }}
# Option 3: Organization projects with GitHub tools integrationtools: github: toolsets: [default, projects] github-token: ${{ secrets.ORG_PROJECT_WRITE }}safe-outputs: update-project: github-token: ${{ secrets.ORG_PROJECT_WRITE }}Notes:
update-project is update-only. It will not create projects. If a project does not exist, the job fails with instructions to create it manually.GITHUB_TOKEN cannot be used for Projects v2 operations. Configure GH_AW_PROJECT_GITHUB_TOKEN or provide a custom token via safe-outputs.update-project.github-token.project scope (plus repo if accessing private repos). Fine-grained PATs do not work with user-owned Projects.project + read:org scopes, or a fine-grained PAT with:
create_if_missing: true in its output, and the token must have sufficient permissions to create projects in the organization.GH_AW_PROJECT_GITHUB_TOKEN for Projects-specific isolation; use GH_AW_GITHUB_TOKEN if it already has Projects permissions and you do not need isolation.GH_AW_AGENT_TOKENIf you want to programmatically assign Copilot agents to issues or pull requests, you need to configure GH_AW_AGENT_TOKEN with a Personal Access Token (PAT) that has the appropriate scopes and permissions for issue and PR management.
Is token/secret is used by assign-to-agent: safe outputs to programmatically assign Copilot agents to issues or pull requests.
Setup:
The required token type and permissions depend on whether you own the repository or an organization owns it:
For User-owned Repositories:
For Organization-owned Repositories:
When an organization owns the repository, you need a fine-grained PAT with the resource owner set to the organization:
Create a fine-grained PAT with:
Add to repository secrets:
gh aw secrets set GH_AW_AGENT_TOKEN --value "YOUR_AGENT_PAT"Token precedence and fallback:
GH_AW_AGENT_TOKEN -> GH_AW_GITHUB_TOKEN -> GITHUB_TOKEN.
Notes:
Two ways to assign Copilot agents
There are two different methods for assigning GitHub Copilot agents to issues or pull requests. Both methods use the same token (GH_AW_AGENT_TOKEN) and GraphQL API to perform the assignment:
assign-to-agent safe output: Use when you need to programmatically assign agents to existing issues or PRs through workflow automation. This is a standalone operation that requires the token documented on this page.safe-outputs: assign-to-agent: name: "copilot" allowed: [copilot]assignees field in create-issue: Use when creating new issues through workflows and want to assign the agent immediately. When copilot is in the assignees list, it is automatically filtered out and assigned via GraphQL in a separate step after issue creation (using the same token and API as method 1).safe-outputs: create-issue: assignees: copilot # or assignees: [copilot, user1]Both methods result in the same outcome as manually assigning issues to Copilot through the GitHub UI. Method 2 is simpler when creating issues, while method 1 provides fine-grained control for existing issues.
Technical implementation: Both methods use the GraphQL replaceActorsForAssignable mutation to assign the copilot-swe-agent bot to issues or PRs. Both follow the token precedence and fallback behavior documented above.
See GitHub’s official documentation on assigning issues to Copilot for more details on the Copilot coding agent.
Resource owner requirements: The token’s resource owner must match the repository ownership:
This ensures the token has the appropriate permissions to assign agents to issues and pull requests in the repository.
For enhanced security with short-lived tokens, you may configure a GitHub App instead of using PATs.
This does not apply to COPILOT_GITHUB_TOKEN, which must currently be a PAT. A single GitHub App can be used for all other GitHub tokens.
After creating your app, there are two ways to configure it in your workflow:
Option 1: Direct configuration (more control)
permissions: contents: read issues: read
tools: github: mode: remote toolsets: [repos, issues, pull_requests] app: app-id: ${{ vars.APP_ID }} private-key: ${{ secrets.APP_PRIVATE_KEY }} owner: "my-org" # Optional: defaults to current repo owner repositories: ["repo1", "repo2"] # Optional: defaults to current repo onlyOption 2: Shared workflow (recommended - centralized configuration)
Use the provided shared workflow for centralized configuration:
imports: - shared/github-mcp-app.md # Provides APP_ID and APP_PRIVATE_KEY configuration
permissions: contents: read issues: read
tools: github: mode: remote toolsets: [repos, issues, pull_requests]The shared workflow (shared/github-mcp-app.md) expects:
APP_ID - Your GitHub App IDAPP_PRIVATE_KEY - Your GitHub App private keySet up repository variables and secrets:
gh variable set APP_ID --body "123456"gh aw secrets set APP_PRIVATE_KEY --value "$(cat path/to/private-key.pem)"How it works:
At workflow start, a token is automatically minted with permissions matching your job’s permissions: field. The token is passed to the GitHub MCP server and automatically revoked at workflow end (even on failure).
This is the same per-job narrowing behavior used by safe-outputs.app: - see the Safe Outputs documentation for a detailed explanation of how GitHub App tokens are narrowed per-job.
Ownership affects token requirements for repositories and Projects (v2). If the owner is your personal username, it is user-owned. If the owner is an organization, it is org-owned and managed with shared roles and access controls.
To confirm ownership, check the owner name and avatar at the top of the page or in the URL (github.com/owner-name/...). Clicking the owner takes you to a personal profile or an organization page, which confirms it instantly. Here are examples of both (left: user-owned, right: org-owned):
User-owned repository

Avatar shows a personal profile icon, URL includes username
Organization-owned repository
Avatar shows organization icon, URL includes org name